After the first post, we are going to establish which tools (operating systems, environments, scripts, etc…) we are going to use when carrying out the different tests to go from one phase to another.
Hypervisor
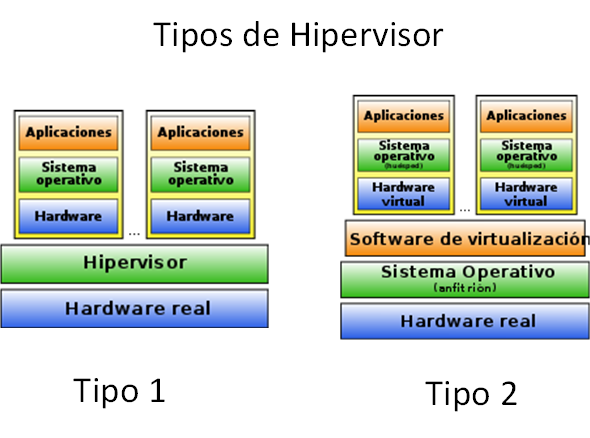
A hypervisor is a software that creates and executes VMs, isolating the operating system and the resources of the physical machine from the VMs; in this way it is possible to allocate the necessary resources according to the VM depending on the free physical resources Source. There are 2 types of hypervisor, depending on the level of abstraction of resources between hardware and virtual systems:
- Type 1 (bare metal)
- It runs directly on the hardware, generating a high level of performance.
- Type 2 (hosted)
- It runs on an operating system obtaining a lower performance because it uses part of the hardware for the use of this one.
Due to the purpose of this task, it will be necessary to choose a virtualisation solution among those available on the market, the most recommendable to obtain greater performance would be to work with a type 1 hypervisor, such as Proxmox Virtual Environment or VMware vSphere, as there are no local servers where these services can be installed, a type 2 hypervisor should be chosen, the best known being VMware Workstation or Oracle VM Virtualbox. A comparison between VMware Workstation and Oracle VM Virtualbox hypervisors can be seen in the following link.
After analysing the above comparison table, it was decided to use VMWare Workstation in version 17.0.0 build-20800274. Although it does not allow software virtualisation, its paid version allows special features such as better compatibility with Windows systems, thanks to the VMWare Tools, making it perform better than VirtualBox. The installation process does not contain any key points of note, except that at the end of the process you must set the authentication key required to use the software.
Vulnerable environment
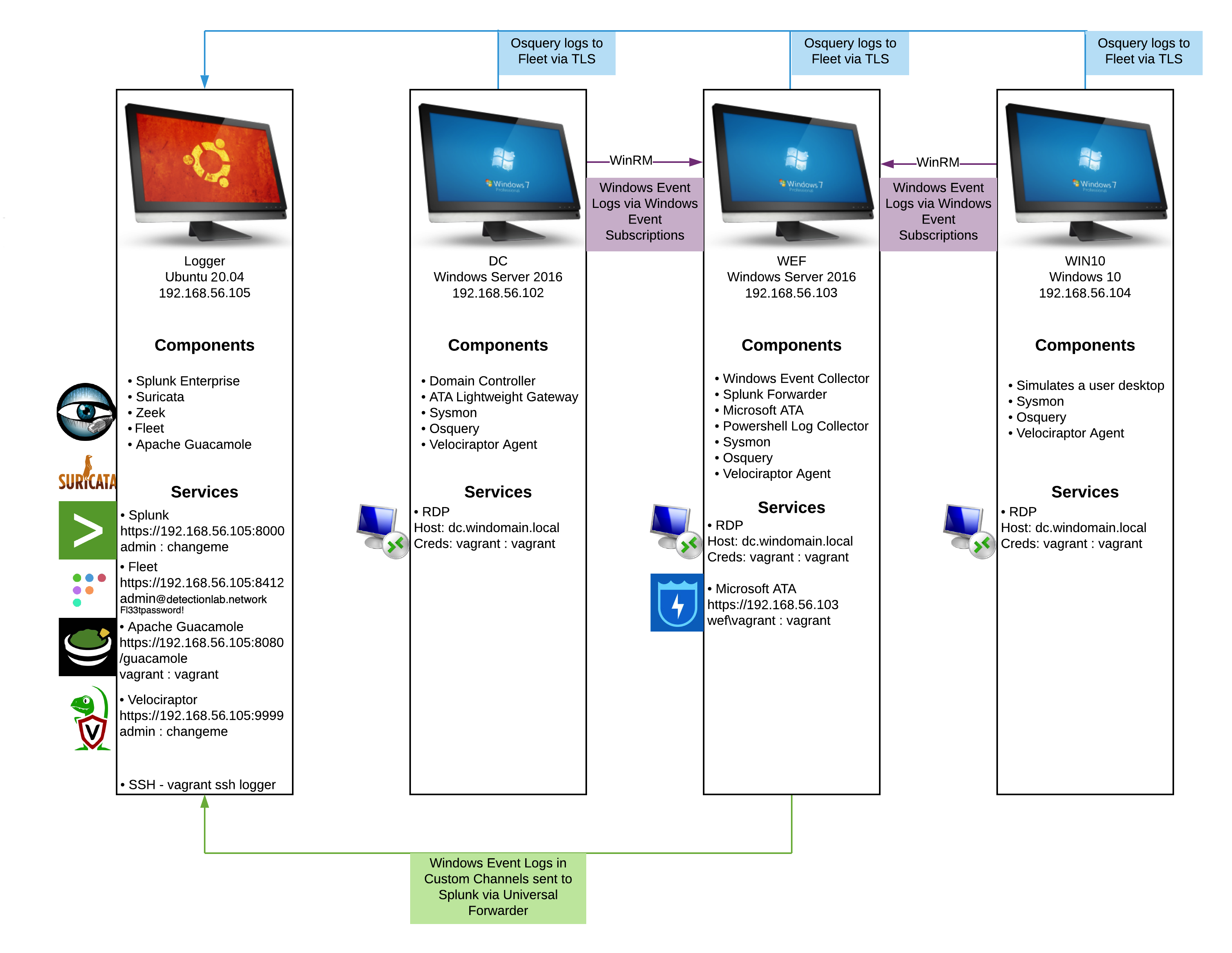
In the first instance, after analysing different sources of the available AD deployment environment, it was decided to use the Detection Lab repository that allows the deployment of an AD scenario on a type 2 hypervisor; it is also possible to deploy it on the cloud, but this would imply a high cost and the execution of penetration tests could be involved in problems due to the configuration of the platforms that defend their assets to the maximum, as well as the need to request permissions to carry out penetration tests.
Although Detection Lab was built with defenders in mind, it serves to run different attack tests, and then simplify defence testing, analysis and investigation.
The final environment that would be deployed is presented in the figure below:
Unfortunately this project has encountered different problems in different releases of this environment, detailed in the project’s Gitgub issues Logger failing to install Zeek and Failed to fix the broken static IP for eth1., which have not been resolved during the execution of this post. In addition, it can be seen that the tool has stopped supporting users since 01/01/2023, so it is doubtful that they will solve the problems indicated, however, I encourage readers to test the execution of the environment using the deployment instructions and check if with the characteristics of your Pc works correctly or have solved the bugs when you are reading it.
For the reason described above, it has been decided to perform the deployment on its own, creating an AD with a Windows Server 2016 and 3 Windows 10 Enterprise, in the LTSC version, as it has no advertising or pre-installed applications. As these are trial versions, no activation serial will be requested.
In the next post we will see the installation process and configuration of the systems.
Pentesting Operating System
There are multiple operating systems focused on offensive security, these are generally distributed under Linux and the main difference with the users’ operating systems are their pre-installed tools focused on cybersecurity.
Kali Linux
It is the best known penetration testing operating system, has extensive documentation and comes with different penetration suites depending on the type of audit performed.
“It is a Debian GNU/Linux based distribution designed primarily for auditing and computer security in general. It was developed by Mati Aharoni and Devon Kearns, both members of the Offensive Security team, who used BackTrack as a base, so it could be called the predecessor of Kali Linux. ” Source
It has different platform images so that different devices with different architectures can run it and adds a huge number of open source tools, some 600 of them, designed for offensive security.
Parrot Security OS
This is a development branch provided by Parrot OS, which is a Debian-based GNU/Linux distribution with a focus on computer security. It is designed for penetration testing, vulnerability assessment and analysis, computer forensics, anonymous web browsing and cryptographic practice, developed by the Frozenbox Team. Source
Like Kali, this operating system provides security tools designed for pentesting, as well as default settings that protect user anonymity on the network.
BlackArch Linux
It is an Arch Linux distribution that allows the execution of penetration tests thanks to its repository with more than 2800; it is intended for advanced users in the Linux environment and was developed by Stefan Venz.
It is analysed that the real difference between the different security operating systems is the tools that come pre-installed and their Linux bases, so it was decided to use the most visually intuitive from my point of view, Parrot Security OS ver 5.1.2. Its installation will be discussed in the next post.
Conclusion
This would be all, in the next post we will see how we will install and configure the whole environment to be vulnerable to the different steps/attacks that the proposed methodology will go through little by little.