Hello everyone,
In this series of posts we are going to detail the best methodology in order to breach an Active Directory.
But, to start from the beginning, what is an Active Directory?
Active Directory (AD)
It is a service that simplifies hierarchies and allows you to store objects for quick and easy access and manipulation. It is developed and maintained by Microsoft, It also allows centralised management of tasks and resources for all users. AD essentially enables the mapping of the structures of an organisation, separating them by domains and units of the structure, along with their objects. Source
AD uses different network protocols such as LDAP, DHCP, KERBEROS and DNS and acts as a database that stores records that are part of the network, centrally identifying the users of the network. centrally identifying the users of the network. Many applications depend directly on an AD, so if this service fails it could cause serious problems for the organisation. For this reason, it is possible to distribute the databases in different servers guaranteeing the availability of the AD at all times. The logical structure of an AD is based on the grouping of elements that are part of a domain up to the elements themselves, which can be users, peripherals or other servers. An AD is composed of the following elements:
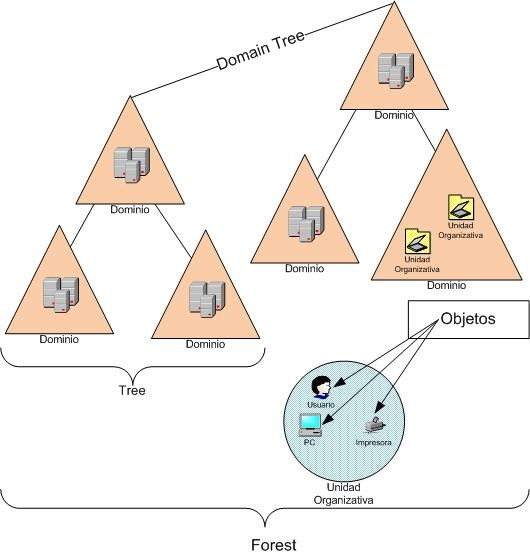
Objects
This is the smallest unit managed by an AD and corresponds to a single entry in the database. It describes resources or devices such as computers, servers, storage devices such as computers, servers, storage, printers, users, groups or file shares; all the characteristics that an object possesses, such as its type object, such as its type, class, properties or syntax are generally defined by a common schema.
Classes
These are the schemas or templates that compose the types of objects, each class unambiguously defines the properties or attributes that compose the object, since each object contains a common schema. object, since each object contains its own combination of all these values.
Schema
This is the logical separation of the network into different domains, as they meet the same conditions and security management.
Organisational units
These are the containers that are responsible for the organisation of the objects.
Domain Controllers
This is the service that controls the authentication of the objects and assigns them the different security configurations. These controllers store all the information of the AD, which makes it essential when logging in and carrying out queries and operations in the AD.
Domain
These are the unique domain names intended to identify the organisation’s structures, following DNS naming conventions, allowing domains and sub-domains to be established for internal structures within a domain.
Domain trees
This is a set of domains where depending on their inclusion in the structure allows them to become the child of a larger domain.
Forest
It is a set of trees that compose the complete service of an AD.
Finally, the AD allows to centrally manage the objects that connect to it through group policies, this administration allows to execute scripts, change the desktop or perform program installations independently, without the user of the object acting. These policies are applied at the different levels provided by the AD, at the site level, at the domain level and at the organizational unit (OU) level. All these settings are taken care of during object startup, every 90 minutes, and depending on the area of application are categorized as Group Policy Object (GPO), if it affects a structure or domain, or Local Group Policy Object (LGPO), if it applies to a specific object.
 https://dc722jrlp2zu8.cloudfront.net/media/uploads/2021/08/10/picture1.png
https://dc722jrlp2zu8.cloudfront.net/media/uploads/2021/08/10/picture1.png
Conclusion
That’s it, in the next post we will see the different tools available that will be used for the proofs of concept.