Hello everyone,
Once the reconnaissance stage is over, for each of the services and operating systems available on each machine, it is necessary to identify how each of them works and the possible vulnerabilities, in order to be able to access the machines with valid credentials.
Introduction
In this phase, all potential vulnerabilities in the audited systems should be searched for and identified. This can be done through the use of weak or default passwords, outdated service vulnerabilities or incorrect configurations that allow normal users to perform tasks with high privileges.
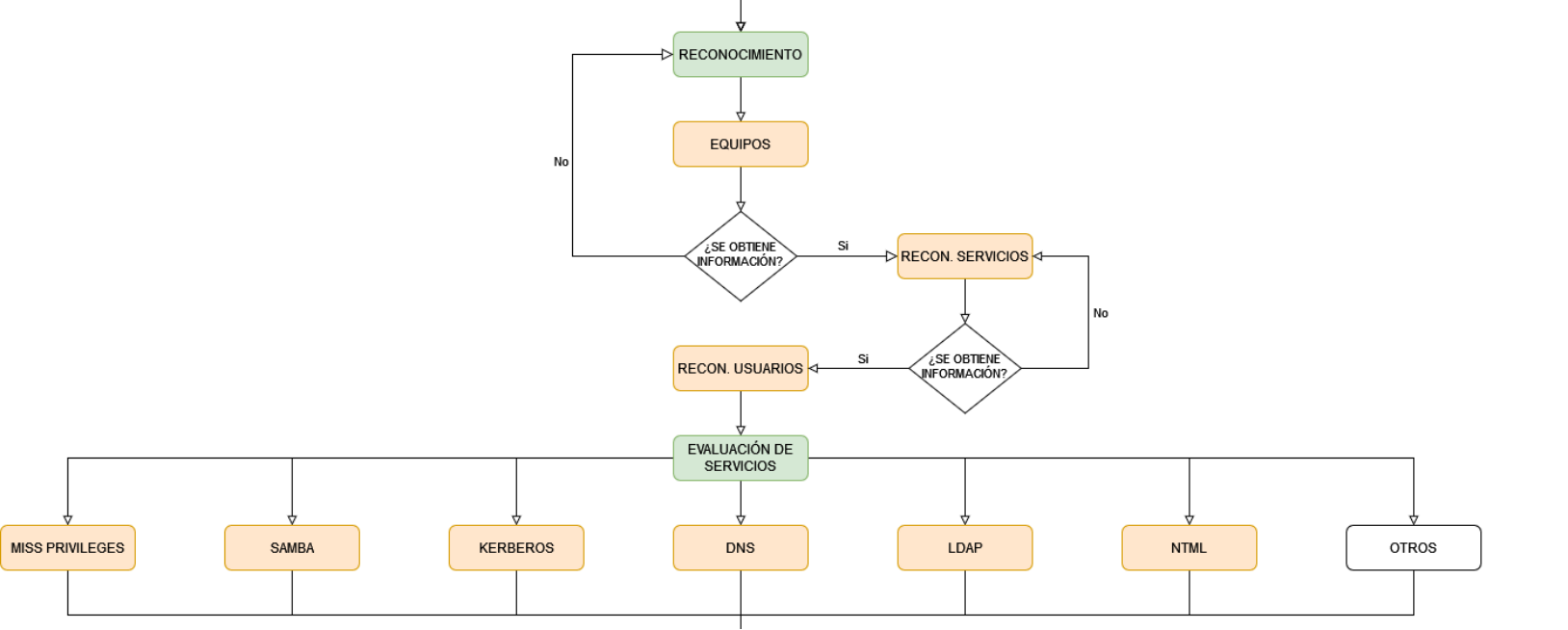
In the following image you can see which services are usually open on the computers when looking for different attack vectors, but you could look for information about any service or attack vector that is open on any of the computers.
Attack Vectors
Kerberos
Kerberos is an authentication protocol (source) for AD clients and servers, usually running on port 88.
Several actors are involved in the use of this protocol (Source):
- User: requesting access to the service.
- Application Server (AP): where the user wants to access the service.
- Key Distribution Centre (KDC): which is in charge of sending tickets to the client from the Domain Controller. It also has a service called AS (Authentication Service) which is responsible for processing the tickets.
In order for the users to be able to carry out the operations that they are allowed to do within the Kerberos domain, it uses a distribution object called tickets, of which there are two types:
- TGS (Ticket Granting Service): it is a ticket granted to a service so that they can access their resources, this type of ticket is encrypted with the key of the service.
- TGT (Ticket Granting Ticket): this is a ticket presented to the KDC necessary to obtain the TGS, this ticket is encrypted with the key of the KDC, derived from the NTLM hash of the krbtgt account.
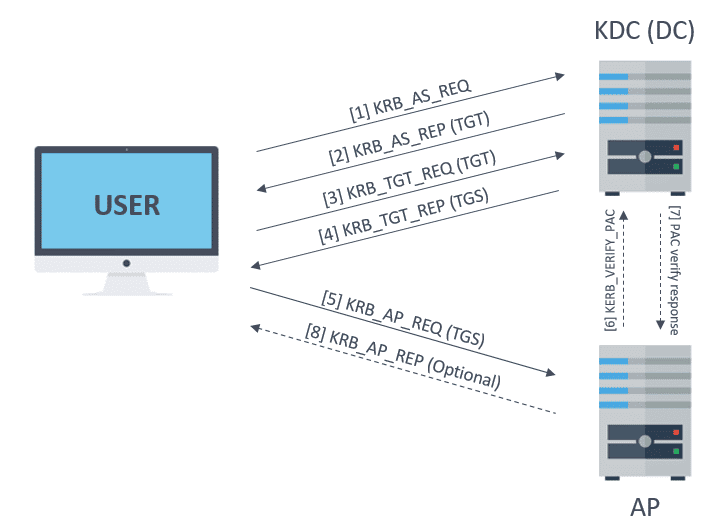
The most common messages transmitted by the protocol during its execution process are:
- KRB_AS_REQ: used to request a TGT from the KDC.
- KRB_AS_REP: is the response from the KDC to deliver the TGT.
- KRB_TGS_REQ: the TGS is requested from the KDC, using the TGT.
- KRB_TGS_REP: this is the response to the TGS request from the user.
- KRB_AP_REQ: used to identify the user in a service by the TGS received.
- KRB_AP_REP: is the response of the service to the user’s authentication.
- KRB_ERROR: used to report errors.
The following image shows the sequence of authentication messages over the protocol. Source:
One of the main problems is that all the information needed by the TGS is included in the Ticket (TGT) issued by the AS, although it is encrypted by the password of the krbtgt account, which makes it the most important in the whole environment, making any information in the TGT untrusted and vulnerable if it is not set correctly. Other vulnerabilities in the protocol are:
Pass The Hash: the pentester obtains the hash of a user, via the file SAM or NTDS.DIT, in order to gain access to the services it has permissions to.
Golden/Silver Ticket: as previously mentioned, this is the most important vulnerability, since the krbtgt user’s hash can be used to construct a TGT that is valid forever until the krbtgt user changes the password.
Kerberoasting: the pentester obtains by different techniques some TGT, which is the one encrypted by the key of the service that manages it, as the key includes the NTLM hash of the user, it would be possible to find the password offline with brute force.
ASREPRoast: this vulnerability uses a user’s attribute configuration, specifically the one that does not request pre-authentication, which allows generating a KRB_AS_REQ message without knowing the user’s credentials and this allows receiving a KRB_AS_REP message, which, as in the previous case, contains the user’s NTLM hash and could be cracked offline.
Samba
It is a protocol for sharing files in Windows environments, it is usually executed on port 445, as it is an implementation of the CIFS protocol for UNIX systems, it allows interconnection with this type of systems so that they can act as Windows clients, finally, it allows the validation of clients by making use of the AD domain. Finally, it allows validating clients by making use of the AD domain.
It is composed of two main services, which is responsible for providing the resources: (Source)
- smbd: this service allows the sharing of resources over an SMB network, it is also in charge of managing the verification and authorisation of users against the resource.
- nmbd: this service is the one that allows the search of resources through Windows Internet Name Service (WINS).
One of the main problems encountered with this service is that it allows user validation, so it sends hashed user credentials to each resource it accesses, and if they are weak, it allows brute-force and offline vulnerability.
Many very important vulnerabilities related to this service have been detected, some of them are: (Source)
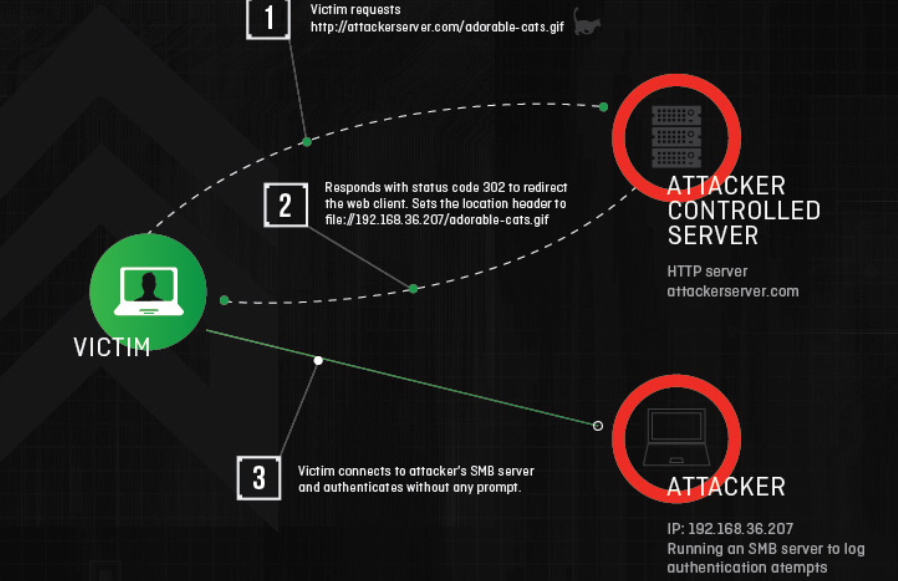
- SMB-Trap: this vulnerability makes use of the URLMon.dll API, which attempts to automatically authenticate the host when a page tries to access a resource via SMB, by sending Hashed Windows credentials. (Source image)
NTLM Theft: the placement of malicious files on a system can trigger an SMB authentication attempt, allowing the NetNTLMv2 hash to be intercepted with some tool.
SMB relay attack: this attack uses network poisoners to capture SMB authentication sessions on an internal network, to relay them to a target machine.
DNS
The DNS protocol is responsible for translating domain names to IP addresses, facilitating the loading of the resource offered, usually present through port 53. A DNS server that translates a client’s internal domain names is not usually exposed on the Internet.
There are different types of DNS servers: (Source)
- Primary: they are responsible for top-level domains (TLDs).
- Secondary: they have authority for a specific zone. They only respond to queries in their area of responsibility and their information is binding.
- Cache: they cache information from other name servers for a certain period of time, indicated by a primary server.
- Forwarders: forward DNS queries to another DNS server.
One of the most known problems with this service is that a user from the DNSAdmins group can inject a DLL and run with SYSTEM privileges, the highest privileges, by including the DLL in a shared resource and restarting the DNS servers.
Another possible attack vector to crash the system hosting the DNS server is through DNS recursion, if enabled, an attacker could spoof the source in the UDP packet to make the DNS send the response to the victim server, thus abusing the ANY or DNSSEC record types.
LDAP
It is a protocol that allows locating resources within a network, public or private, usually running on ports: 389, 636, 3268, 3269.
The directory of resources can be distributed among many servers (Source), replicating the main directory and synchronising from time to time.
An LDAP server is called a Directory System Agent (DSA), which is responsible for receiving user requests, forwarding them to other DSAs if necessary, and responding to user requests.
The directory is organised in a tree structure, starting at the root directory, branching into countries, each divided into organisations, extending into organisational units, and finally branching into different resources, such as files, people or shares.
Some of the problems encountered in LDAP is the lack of encryption in LDAP queries, which results in sending credentials in clear text. Also a MITM attack can downgrade the protocol version to send credentials in plaintext; furthermore, a fake certificate can be offered to present the resources and if accepted receive credentials in plaintext.
Finally, with valid credentials it is possible to obtain all information about the domain administrator.
NTLM
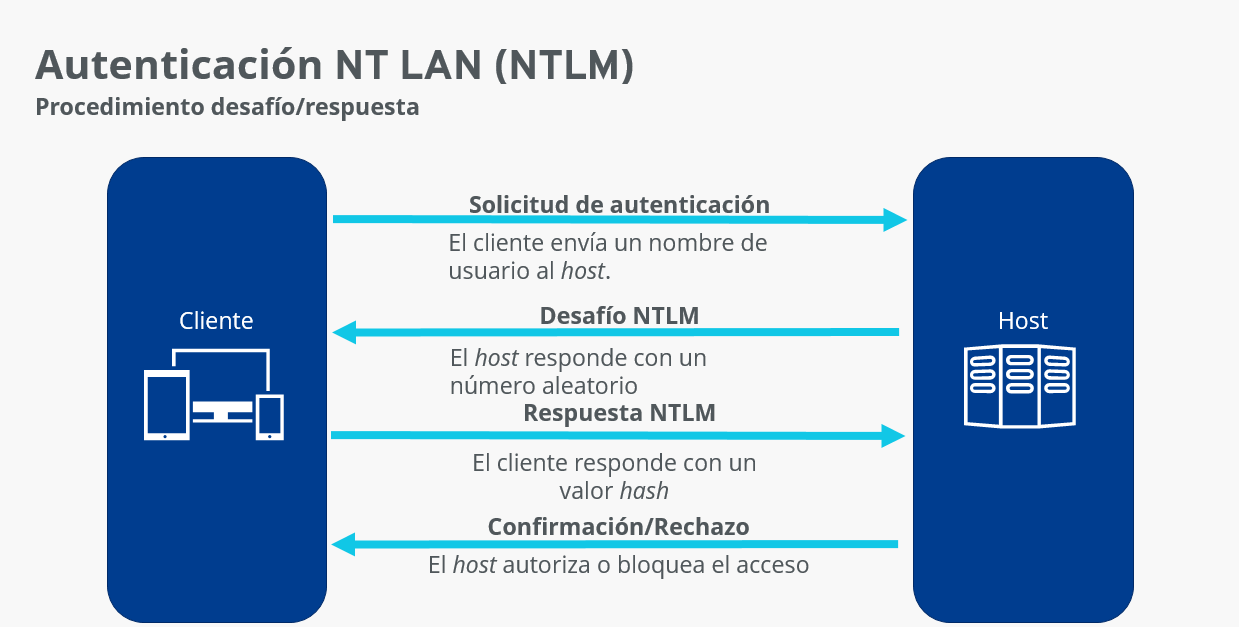
It is an authentication protocol that allows different computers and servers to verify each other using hashes. Source
NTLM uses a process called challenge/response that handles authentication, the steps it follows can be seen in the following figure:
The most common NTLM attack is credential theft (Source), accessing shared resources with a null or guest user could place files that trigger an NTLM authentication against the attacker and then crack it offline.
Another attack is NTLMRelay, which relays SMB authentication sessions on an internal network to another machine, if the credentials sent are correct, access to the target is gained, these credentials must be from an administrator of the machine and the SMB signature must be disabled.
Miss privileges
Sometimes the privileges granted to roles or users can lead to security problems if their credentials are breached (Source). There are different privileges that are granted to users so that they can perform different actions within an AD, however, these actions can trigger theft of credentials in memory or access to other users’ processes, without the need to be administrators.
A vulnerability within the backup privilege lies in the permissions it grants, which include browsing any folder and listing its contents. It will also allow copying a file from a folder, without permissions.
Conclusion
This is all, in the next post we will go into the execution of the attack vectors available on the environment.